Table of Contents
I. Introduction
In modern networking environments, understanding the concept of Native VLAN and its configuration on Cisco switches is crucial for efficient network management and security. The Native VLAN plays a significant role in handling untagged traffic within a VLAN trunk, and proper configuration is essential to ensure smooth inter-VLAN communication. This blog post delves into the intricacies of Native VLAN, its significance, and best practices for configuring it in Cisco networks.
II. What is Native VLAN?
The Native VLAN is a fundamental concept in Virtual LANs (VLANs) used to designate an untagged VLAN within a trunked network. In Cisco networks, a trunk port carries traffic from multiple VLANs, and the frames of each VLAN are distinguished by their respective VLAN tags. However, there is always one VLAN in a trunk that remains untagged, known as the Native VLAN. Unlike other VLANs, frames in the Native VLAN do not have VLAN tags, and they are transmitted untagged across the trunk link.
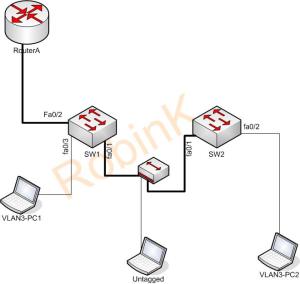
In Cisco switches, by default, VLAN 1 is assigned as the Native VLAN on trunk ports. However, it is essential to configure the Native VLAN explicitly to ensure optimal network performance and security.
III. Native VLAN Configuration
Configuring the Native VLAN on Cisco switches is a straightforward process that involves specifying the VLAN ID for the Native VLAN on trunk ports. This configuration allows the switch to understand which VLAN should remain untagged while transmitting data over the trunk link.
switchport trunk native vlanThe “switchport trunk native vlan” command is used to set the Native VLAN ID on a Cisco switch trunk port. Administrators can assign any VLAN ID (other than the default VLAN 1) as the Native VLAN, based on their network requirements.
switchport mode trunkAdditionally, the “switchport mode trunk” command is used to configure the port as a trunk port to carry multiple VLANs, including the Native VLAN.
By explicitly configuring the Native VLAN, network administrators can avoid potential security risks and ensure efficient traffic flow within the network.
IV. Understanding Native VLAN Mismatch
A Native VLAN mismatch occurs when the Native VLAN configured on one end of a trunk link does not match the Native VLAN configured on the other end. This misconfiguration can lead to several network issues, including data leakage, traffic misdirection, and potential security vulnerabilities.
In a scenario with Native VLAN mismatch, untagged frames from one VLAN may be received and interpreted as belonging to a different VLAN on the other end of the trunk. This can result in data from one VLAN being mistakenly sent to another, causing communication errors and potential data breaches.
To avoid Native VLAN mismatch, network administrators must ensure consistent Native VLAN configuration on both ends of a trunk link. Regular audits and verification of Native VLAN settings are essential to maintain a secure and reliable network.
V. Native VLAN vs Default VLAN
Although the Native VLAN and Default VLAN are both crucial components of VLAN configurations, they serve different purposes within Cisco networks.
The Native VLAN
- Handles untagged traffic within a trunked network.
- Needs to be explicitly configured on trunk ports to ensure consistency.
- Should be chosen carefully to prevent security risks and data miscommunication.
The Default VLAN
- Serves as the initial VLAN for all switch ports that are not explicitly assigned to a specific VLAN.
- Often, VLAN 1 is set as the Default VLAN by default in Cisco switches.
- Has the potential to pose security risks if left unchanged or unused.
It is important to understand the distinction between the Native VLAN and Default VLAN to implement proper network segmentation and minimize security vulnerabilities.
| Aspect | Native VLAN | Default VLAN |
|---|---|---|
| Purpose | Facilitates untagged traffic | Acts as a fallback for untagged packets |
| VLAN ID | Configurable (User-defined) | VLAN 1 (Fixed default VLAN) |
| Trunk Port Behavior | Carries untagged frames | Carries untagged and tagged frames |
| Security Implication | Can pose security risks | Should be used with caution |
VI. Importance of Native VLAN in Network Security
The Native VLAN plays a significant role in network security by facilitating proper handling of untagged traffic within a VLAN trunk. Proper configuration of the Native VLAN prevents unauthorized access to VLANs and helps maintain network isolation.
An untagged frame entering a trunk port is assumed to belong to the Native VLAN. If the Native VLAN is left as the default VLAN 1, an attacker with physical access to the network could gain access to sensitive data by sending untagged frames. However, by explicitly configuring a non-default Native VLAN and implementing proper access control measures, such security risks can be mitigated.
Furthermore, Native VLAN configuration helps prevent Native VLAN hopping attacks, where an attacker attempts to exploit misconfigured trunk ports to gain unauthorized access to other VLANs. By selecting an appropriate Native VLAN and ensuring consistency across trunk links, network administrators can enhance network security and protect sensitive information.
VII. Is Native VLAN Necessary?
The necessity of configuring the Native VLAN in Cisco networks depends on specific network requirements and security considerations. While some network setups may function adequately without explicit Native VLAN configuration, it is highly recommended to set a dedicated Native VLAN for enhanced network control and security.
Leaving the Native VLAN as the default VLAN 1 can pose significant security risks, as it allows untagged frames to traverse the network without any VLAN isolation. This could potentially lead to unauthorized access, data interception, and network breaches.
By configuring a non-default Native VLAN and applying proper access control lists (ACLs) and VLAN-based policies, network administrators can enforce strict separation between VLANs, reducing the attack surface and improving network security.
In summary, while Native VLAN configuration might not be mandatory in all scenarios, it is a prudent practice for maintaining a robust and secure network infrastructure.
VIII. Best Practices for Native VLAN Configuration
To ensure efficient and secure network operation, network administrators should follow these best practices when configuring the Native VLAN on Cisco switches:
- Explicit Configuration: Avoid relying on the default Native VLAN (VLAN 1) and explicitly set a dedicated VLAN ID for the Native VLAN on trunk ports.
- Consistency Across Trunk Links: Ensure that the Native VLAN configuration remains consistent across all trunk links in the network to prevent Native VLAN mismatch issues.
- Security Considerations: Choose a Native VLAN ID that aligns with your network’s security policies and apply proper access controls to restrict unauthorized access.
- Regular Audits: Periodically audit and verify the Native VLAN settings on all trunk ports to detect and rectify any misconfigurations promptly.
- Documentation: Maintain detailed documentation of Native VLAN configurations, including VLAN IDs and port assignments, for easier troubleshooting and network management.
IX. Troubleshooting Native VLAN Issues
When encountering Native VLAN-related issues, consider the following troubleshooting steps:
- Native VLAN Mismatch: Verify that the Native VLAN ID matches on both ends of trunk links. Reconfigure the Native VLAN if necessary.
- Unintended Native VLAN Traffic: Check for unauthorized devices or untagged traffic entering trunk ports. Implement port security measures to prevent unauthorized access.
- Security Breaches: Investigate any signs of data leakage or unauthorized access. Analyze access control measures and adjust them as needed.
- VLAN Hopping Attacks: Inspect trunk port configurations for potential vulnerabilities. Implement best practices to mitigate VLAN hopping risks.
X. Conclusion
In conclusion, understanding and properly configuring the Native VLAN in Cisco networks are critical for network segmentation, security, and smooth data flow. Explicitly setting a dedicated Native VLAN, avoiding default VLAN 1, and adhering to best practices enhance network performance and reduce security risks. By following these guidelines and conducting regular audits, network administrators can maintain a secure and efficient network infrastructure that aligns with industry standards and best practices.
XI. FAQs (Frequently Asked Questions)
A. What is the purpose of Native VLAN in Cisco networks?
The Native VLAN in Cisco networks serves as the designated VLAN for handling untagged traffic within a trunked network. It allows for seamless communication between devices that do not support VLAN tagging. Additionally, the Native VLAN plays a crucial role in network security by providing a means to segregate and isolate untagged frames, preventing unauthorized access and data breaches.
B. How to configure Native VLAN on a Cisco switch?
To configure the Native VLAN on a Cisco switch, follow these steps:
- Access the switch’s configuration mode using the Command Line Interface (CLI).
- Identify the trunk port on which you want to configure the Native VLAN.
- Use the “switchport trunk native vlan” command followed by the desired VLAN ID to set the Native VLAN for the trunk port.
- Save the configuration changes using the appropriate command (e.g., “write memory” or “copy running-config startup-config”).
Remember to apply the same Native VLAN configuration on both ends of the trunk link to avoid Native VLAN mismatch.
C. What is the difference between Native VLAN and Default VLAN?
The Native VLAN and Default VLAN serve distinct purposes in VLAN configurations:
- Native VLAN: Designates the VLAN that carries untagged frames within a trunked network. It is explicitly configured on trunk ports and plays a crucial role in inter-VLAN communication.
- Default VLAN: Serves as the initial VLAN for all switch ports that are not explicitly assigned to a specific VLAN. VLAN 1 is typically set as the default VLAN by default in Cisco switches. Unlike the Native VLAN, the Default VLAN is not explicitly configured on trunk ports and is often used as a fallback VLAN for untagged packets.
D. Why is Native VLAN mismatch a concern and how to fix it?
Native VLAN mismatch occurs when the Native VLAN configuration on one end of a trunk link does not match the configuration on the other end. This mismatch can lead to communication errors, data misdirection, and security vulnerabilities.
To fix a Native VLAN mismatch, verify and ensure consistent Native VLAN settings on both ends of the trunk link. Update the Native VLAN configuration on the affected ports to match the desired VLAN ID. Regular audits and verification of Native VLAN settings are essential to prevent Native VLAN mismatch issues.
E. Is Native VLAN necessary for network security?
Configuring a dedicated Native VLAN is highly recommended for network security. Leaving the Native VLAN as the default VLAN 1 can pose security risks, allowing untagged frames to traverse the network without proper VLAN isolation.
By explicitly configuring a non-default Native VLAN and applying access control measures, network administrators can enhance network security, prevent unauthorized access, and mitigate potential security threats. Proper Native VLAN configuration is an important aspect of securing VLAN trunking in Cisco networks.

1 thought on “Understanding Native VLAN and Free Cisco Configuration”