Table of Contents
I. Introduction
In the ever-evolving world of networking, Software-Defined Access (SD-Access) has emerged as a game-changer, revolutionizing the way networks are designed, deployed, and managed. This cutting-edge technology brings automation, flexibility, and enhanced security to network infrastructures, enabling organizations to thrive in the digital era.
A. What is SD-Access?
Software-Defined Access (SD-Access) is a transformative networking technology that harnesses the power of software-defined principles to create a cohesive and dynamic network fabric. At its core, SD-Access aims to simplify network operations, enhance security, and provide scalability for modern network infrastructures.
One of the key aspects of SD-Access is the decoupling of the control plane from the data plane. By centralizing network control, SD-Access allows for policy-based control and centralized management, leading to streamlined operations and increased efficiency. This centralized approach empowers organizations to automate network provisioning, making it easier to adapt to changing business needs and reducing the risk of manual errors.
Moreover, SD-Access enables organizations to achieve better network segmentation and access control through the implementation of virtual networks and policies. This enhanced security posture ensures that sensitive data and critical assets are safeguarded, mitigating potential cybersecurity threats.
B. The Evolution of Networking Technologies
To truly grasp the significance of SD-Access, it’s important to look back at the evolution of networking technologies. Traditional networking relied heavily on manual configurations, where network administrators had to configure each network device individually. This approach was time-consuming and error-prone, hindering the agility and responsiveness of network infrastructures.
The emergence of Software-Defined Networking (SDN) brought a revolutionary change to networking. SDN introduced the concept of decoupling the control plane from the data plane, enabling centralized control and programmability. This newfound flexibility allowed network administrators to adapt their networks more efficiently to meet business requirements.
Taking a step further, SD-Access builds upon the principles of SDN and extends them to the access layer of the network. By doing so, SD-Access creates a unified and seamless network fabric, providing a more comprehensive and holistic approach to network management and security.
C. Importance and Benefits of SD-Access
SD-Access brings a plethora of benefits to organizations seeking to optimize their network infrastructure. One of the primary advantages is simplified network provisioning and operations. With centralized management and automation, SD-Access reduces the complexity of managing a large-scale network, allowing network administrators to focus on strategic initiatives.
Another crucial benefit of SD-Access is increased network visibility and troubleshooting efficiency. By providing real-time insights into network performance and user behavior, SD-Access empowers administrators to proactively identify and resolve potential issues, ensuring optimal network performance and user experience.
Furthermore, SD-Access enhances network security and policy enforcement. Through network segmentation and granular access controls, organizations can establish strict security policies and protect critical assets from unauthorized access and cyber threats.
Scalability and flexibility are also key advantages of SD-Access. As organizations grow and expand their network infrastructure, SD-Access accommodates these changes seamlessly, making it easier to adapt to evolving business demands and technological advancements.
II. Key Components of SD-Access
SD-Access comprises several critical components that work together to create a robust and efficient network infrastructure. Let’s delve into these key elements:
A. SD-Access Fabric: Building the Foundation
At the heart of SD-Access lies the fabric, a unified network architecture that spans across the entire enterprise. The fabric is responsible for connecting all network devices, including switches and access points, and enables seamless communication and policy enforcement. Leveraging the fabric, organizations can achieve simplified network designs, reduced complexity, and better scalability.
The fabric operates based on a hierarchical structure, consisting of three main layers: the Fabric Border Layer, the Control Plane Layer, and the Fabric Edge Layer. Each layer plays a crucial role in providing secure and reliable network connectivity to users and devices.
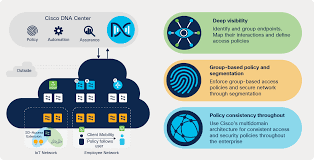
Image Credit: cisco.com
B. DNA Center: Centralized Management
Cisco’s Digital Network Architecture (DNA) Center serves as the centralized management platform for SD-Access. This powerful tool offers a single pane of glass for network administrators to manage and monitor the entire SD-Access fabric. From DNA Center, administrators can define network policies, deploy configurations, and gain valuable insights into network performance.
DNA Center also facilitates policy-based automation, enabling organizations to define intent-based policies that automatically translate into network configurations. This streamlined approach drastically reduces manual configuration efforts and human errors, freeing up valuable time for network teams to focus on strategic initiatives.
C. Identity Services Engine (ISE): Enhanced Security and Access Control
Security is a paramount concern for any network environment, and SD-Access excels in this aspect through the implementation of Cisco’s Identity Services Engine (ISE). ISE serves as the policy engine for SD-Access, providing robust access control and authentication mechanisms.
With ISE, organizations can implement granular access policies based on user identities, device types, and other contextual attributes. This ensures that only authorized users and devices gain access to specific resources within the network, bolstering the overall security posture.
Moreover, ISE enables dynamic segmentation, a critical capability for implementing zero-trust security models. By dynamically segmenting the network based on user and device attributes, organizations can isolate and protect critical assets, mitigating the potential impact of security breaches.
D. Assurance and Analytics: Gaining Insights for Network Optimization
To achieve optimal network performance and user experience, SD-Access provides advanced assurance and analytics capabilities. Through real-time monitoring and analytics, network administrators can gain valuable insights into network behavior, traffic patterns, and user activities.
This data-driven approach empowers organizations to proactively identify and address performance issues, ensuring a smooth and seamless network experience for end-users. Additionally, assurance and analytics enable better capacity planning, helping organizations make informed decisions about network upgrades and expansions.
III. Exploring SD-Access Benefits
With a understanding of the key components, let’s now explore the wide-ranging benefits that SD-Access brings to modern network infrastructures.
A. Simplified Network Provisioning and Operations
SD-Access simplifies network provisioning and operations by centralizing management and automating configuration tasks. With a single management platform like DNA Center, network administrators can define intent-based policies and apply them consistently across the entire fabric. This streamlined approach reduces the risk of configuration errors and accelerates the deployment of new services.
B. Increased Network Visibility and Troubleshooting Efficiency
The assurance and analytics capabilities of SD-Access provide administrators with unparalleled network visibility. Real-time monitoring and analytics allow administrators to monitor network performance, identify anomalies, and troubleshoot issues promptly. This proactive approach ensures optimal network performance and minimizes downtime.
C. Enhanced Network Security and Policy Enforcement
SD-Access enhances network security by implementing dynamic segmentation and access control policies. By leveraging ISE and the fabric’s capabilities, organizations can enforce strict security policies based on user identity and device attributes. This helps prevent unauthorized access and reduces the attack surface, enhancing overall network security.
D. Scalability and Flexibility for Growing Networks
As organizations evolve and expand, SD-Access offers the scalability and flexibility to adapt to changing business needs. The fabric’s hierarchical design and automated provisioning allow for seamless network expansion and integration of new devices and services.
IV. Understanding SD-Access Compatibility
Ensuring smooth integration and compatibility is crucial when adopting SD-Access in an existing network infrastructure. Let’s explore the factors related to compatibility:
A. Compatibility Matrix: Ensuring Smooth Integrations
Before implementing SD-Access, it is essential to verify the compatibility of existing network devices with the fabric. Cisco provides a compatibility matrix that outlines the supported hardware and software versions for seamless integration. This matrix helps organizations identify any potential limitations or upgrade requirements to ensure a successful SD-Access deployment.
Cisco SDA Compatibility Matrix
B. Supported Hardware and Software Platforms
SD-Access is designed to work with a wide range of Cisco networking devices. However, it is essential to ensure that the switches, routers, and access points in the network are compatible with SD-Access. Older hardware platforms may require firmware updates or may not fully support all SD-Access features. As a best practice, organizations should check Cisco’s documentation for the latest information on supported hardware and software platforms.
V. SD-Access Deployment Considerations
Before embarking on an SD-Access deployment journey, network professionals need to carefully consider certain aspects to ensure a successful implementation:
A. Preparing for SD-Access Implementation
Proper planning is essential before implementing SD-Access. This involves assessing the current network infrastructure, identifying potential challenges, and defining the desired outcomes. A thorough understanding of business requirements and network goals will help create a tailored SD-Access deployment strategy.
B. Best Practices and Recommendations
Cisco provides best practices and guidelines to ensure a smooth and successful SD-Access deployment. Following these recommendations helps avoid common pitfalls and ensures the network is optimized for performance, security, and scalability.
VI. The Future of Networking with SD-Access
As organizations embrace digital transformation and the demands for agile, secure, and scalable networks continue to grow, SD-Access is poised to play a pivotal role in shaping the future of networking. Let’s explore the future possibilities of SD-Access:
A. Predictions and Trends in Network Technology
The networking landscape is ever-evolving, and SD-Access is at the forefront of this transformation. As technology advances, we can expect SD-Access to evolve with it, incorporating new features and capabilities to meet the changing needs of modern networks. Trends like multi-cloud adoption, IoT proliferation, and the rise of edge computing will likely influence the development of SD-Access solutions, making them more adaptive and flexible.
B. Embracing SD-Access in the Digital Era
In the digital era, where networks are no longer just a means of connectivity but an enabler of innovation and growth, SD-Access will become a critical enabler for organizations to thrive. Its ability to simplify network operations, enhance security, and enable seamless scalability positions it as a strategic investment for enterprises of all sizes. As more businesses realize the benefits of SD-Access, its adoption is likely to become widespread across various industries.
VII. FAQs (Frequently Asked Questions)
To shed further light on SD-Access and address common queries, here are some frequently asked questions:
A. What is SD-Access, and how does it transform networking?
SD-Access, or Software-Defined Access, is an innovative networking solution from Cisco that leverages automation and virtualization technologies to streamline network operations. It simplifies network provisioning, enhances security, and improves troubleshooting efficiency, making it an ideal choice for modern enterprise networks.
B. Which elements of SD-Access operate outside the fabric?
While most components of SD-Access operate within the fabric, the Identity Services Engine (ISE) and the Cisco DNA Center are elements that function outside the fabric. ISE provides enhanced security and access control, while the DNA Center serves as the centralized management and control platform for SD-Access.
C. How can I ensure compatibility while deploying SD-Access?
To ensure compatibility, organizations must refer to Cisco’s compatibility matrix, which outlines the supported hardware and software platforms for SD-Access. This matrix helps identify any potential limitations and ensures a smooth integration of SD-Access into the existing network infrastructure.
VII. Conclusion
SD-Access has emerged as a transformative technology that revolutionizes how networks are designed, deployed, and operated. With its comprehensive set of features, centralized management, and enhanced security capabilities, SD-Access is a powerful solution for organizations seeking to build agile, scalable, and secure networks.
As the digital era unfolds, SD-Access will continue to evolve and shape the future of networking, ushering in a new era of connectivity and innovation. Embracing SD-Access will be crucial for organizations looking to stay ahead in an increasingly dynamic and competitive business landscape.

2 thoughts on “Understanding Cisco SD-Access(SDA): A Comprehensive Guide for CxO and Architects”