In today’s rapidly evolving digital landscape, where cyber threats loom larger than ever, safeguarding your digital environment against malware attacks has become an imperative. This is where Cisco Advanced Malware Protection (AMP) steps in as a formidable guardian, offering cutting-edge solutions to fortify your cybersecurity defenses.
Table of Contents
I. Introduction
A. Exploring Cisco AMP – Advanced Malware Protection
Cisco AMP represents a groundbreaking advancement in the realm of cybersecurity. It includes a range of cutting-edge technologies intended to find, examine, and eliminate sophisticated malware and other online dangers that conventional security methods could overlook. By utilizing cutting-edge approaches, Cisco AMP offers enterprises a solid defense against the malware landscape’s constant change.
B. Significance of AMP in Modern Cybersecurity
The significance of Cisco AMP cannot be overstated in the context of modern cybersecurity. With the proliferation of sophisticated cyber attacks that exploit vulnerabilities in traditional defenses, the need for a proactive and dynamic approach to malware protection is paramount. Cisco AMP fills this crucial gap by delivering real-time threat intelligence and rapid response capabilities, ensuring that organizations can stay one step ahead of cyber adversaries.
| Aspect | Cisco AMP – Advanced Malware Protection | Traditional Antivirus |
|---|---|---|
| Detection Method | Uses global threat intelligence, machine learning, and behavioral analysis to detect both known and unknown threats. | Relies on signature-based detection primarily for known malware. |
| Malware Prevention | Provides proactive protection by blocking malware at multiple stages of the attack chain. | Often reactive and may require frequent updates to catch new malware variants. |
| File Analysis | Performs dynamic analysis in a secure cloud sandbox to analyze files and identify malicious behavior. | Limited file analysis, usually based on file signatures. |
| Real-time Threat Hunting | Offers real-time threat hunting capabilities to identify and respond to advanced threats. | Lacks real-time threat hunting and may miss sophisticated attacks. |
| Endpoint Visibility | Provides detailed visibility into endpoint activity and advanced threat indicators. | Limited visibility beyond basic malware detection. |
| Integration with Network Security | Integrates seamlessly with Cisco network security solutions for coordinated threat response. | May lack integration with network security components. |
| Behavior-based Protection | Monitors and blocks suspicious behaviors and activities that indicate potential threats. | Focuses mainly on file-level scanning and signature matching. |
| Cloud-based Management | Offers centralized cloud-based management for easy deployment and scalability. | Management may be more complex and on-premises. |
| Protection Against Zero-day Attacks | Offers robust protection against zero-day and unknown threats with sandboxing and machine learning. | Limited zero-day protection and may rely on heuristics. |
| Performance Impact | Optimized for minimal performance impact while providing strong security. | Performance impact can be more noticeable, especially during scans. |
| Incident Response | Assists in incident response with detailed threat intelligence and recommended actions. | Limited incident response guidance. |
| Integration with EDR | Integrates with Cisco Endpoint Detection and Response (EDR) for advanced threat hunting and response. | May lack integration with EDR solutions. |
| Enterprise Scalability | Scales effectively to protect large-scale enterprise environments. | May face challenges in scaling to larger enterprise networks. |
| Cost-effectiveness | Offers cost-effectiveness through advanced threat prevention and reduced incident response time. | May require additional tools and resources for effective threat prevention. |
II. Cisco AMP: Unveiling the Core
A. What is Cisco AMP?
Cisco AMP is an integrated security platform that goes beyond conventional antivirus solutions. It employs a multi-faceted approach that combines advanced detection mechanisms, continuous monitoring, and immediate remediation to combat a wide spectrum of malware threats. By analyzing file behaviors and identifying malicious patterns, Cisco AMP offers a comprehensive defense strategy against both known and emerging malware.
B. Key Components of Cisco AMP
At the heart of Cisco AMP’s efficacy are its key components, each contributing to a holistic defense strategy. The Cisco AMP for Endpoints ensures that every device is protected, while the Cisco AMP for Networks extends threat detection capabilities to the network level. The Cisco AMP for Email Security guards against malware infiltrating through email attachments. Furthermore, Cisco ThreatGrid empowers security teams with advanced threat intelligence, enabling proactive threat hunting and analysis.
C. How Cisco AMP Mitigates Malware Threats
Cisco AMP employs a multi-layered approach to mitigate malware threats effectively. It begins with advanced malware detection, using techniques like file reputation analysis and sandboxing to identify malicious files. Once a threat is detected, Cisco AMP takes swift action through automated blocking, quarantining, and removal of malicious files. Continuous monitoring and analysis ensure that threats are neutralized, and security measures are continually refined.
At the heart of Cisco AMP’s effectiveness are its key components, each contributing to its comprehensive defense mechanism:
- Malware Detection: AMP employs advanced techniques to identify malware, including signature-based detection, behavioral analysis, and sandboxing.
- Threat Intelligence: Powered by Cisco Talos, one of the most formidable threat intelligence teams globally, AMP receives real-time updates on emerging threats and indicators of compromise (IoCs).
- Behavioral Analysis: Cisco AMP meticulously analyzes the behavior of files and processes, identifying anomalies and suspicious activities that hint at potential malware.
- Sandboxing Technology: Suspect files are subjected to sandboxing, a controlled environment where their behavior is observed, providing insights into their intent.
- Centralized Management: AMP offers a centralized console where administrators can monitor and manage security policies, incidents, and response actions.
III. Navigating the Cisco AMP Console
A. Cisco AMP Console: An Overview
The Cisco AMP Console serves as the centralized command center for managing and monitoring your organization’s cybersecurity landscape. It provides a comprehensive view of your security posture, displaying real-time threat alerts, visualizations, and actionable insights. With an intuitive interface, security teams can swiftly assess the status of endpoints, network traffic, and email security, making informed decisions to thwart potential threats.
B. Understanding the Cisco AMP Dashboard
The Cisco AMP Dashboard is a visual representation of your organization’s security landscape. Through customizable widgets and graphical elements, it presents a snapshot of ongoing security activities, threat trends, and mitigation efforts. From a high-level overview to granular details, the dashboard empowers security professionals to detect anomalies, track incidents, and respond promptly.

C. Exploring the Cisco AMP Portal
The Cisco AMP Portal extends the capabilities of the console to provide a comprehensive threat intelligence hub. It aggregates data from diverse sources, including global threat feeds and Cisco Talos, to deliver real-time insights into the threat landscape. Security teams can access threat details, research findings, and recommended actions, facilitating proactive defense strategies.
D. Leveraging the Cisco AMP Endpoints Connector
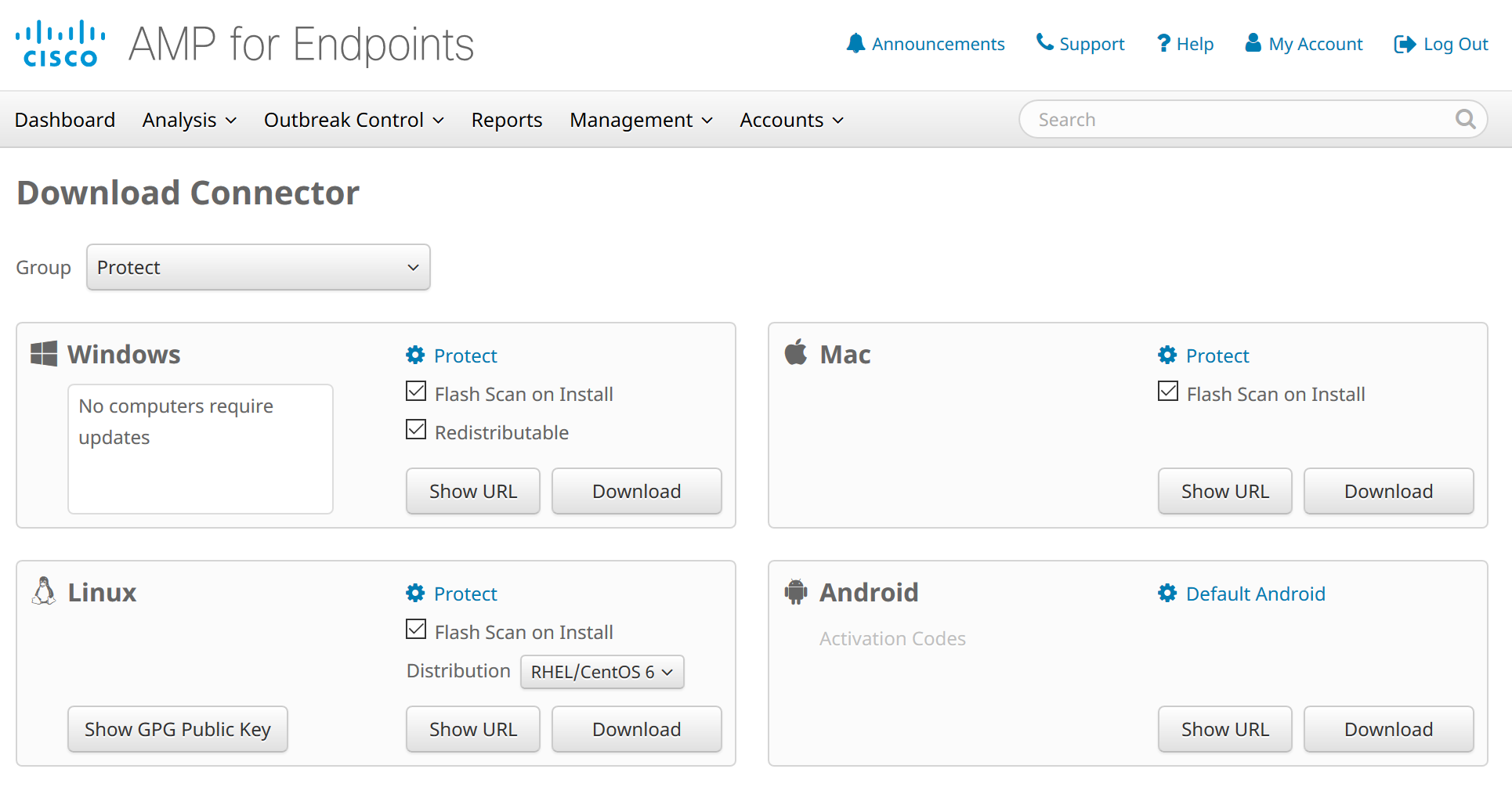
The Cisco AMP for Endpoints Connector facilitates seamless integration between Cisco AMP and endpoint devices. By installing the connector on each endpoint, organizations gain real-time visibility into endpoint activities and potential threats. This integration empowers security teams to respond swiftly to incidents, isolate compromised devices, and initiate remediation measures from the central console.
To download the Cisco AMP for Endpoints Connector, follow these steps:
- Visit the Cisco AMP Console: Go to the Cisco Advanced Malware Protection (AMP) Console using a web browser. Log in with your credentials.
- Navigate to Management: Once logged in, navigate to the “Management” section. Look for an option related to “Download Connector”.
- Download Connector: In the Connectors section, you should find the option to download the Cisco AMP for Endpoints Connector. Click on the download link or button provided.
- Select Operating System: Choose the appropriate operating system for your endpoints. Cisco AMP for Endpoints Connector is available for various operating systems, including Windows, macOS, and Linux.
- Download and Install: After selecting the operating system, the download process will begin. Once the download is complete, locate the downloaded file and run the installer.
- Follow Installation Prompts: The installer will guide you through the installation process. Follow the on-screen prompts to install the connector on your endpoints.
- Activate Connector: During installation, you may be prompted to enter your Cisco AMP Console credentials or an activation key. This step is crucial for the connector to establish a connection with the console.
- Complete Installation: Once the installation is complete and the connector is activated, it will start communicating with the Cisco AMP Console, providing real-time threat data and enabling centralized management.
- Monitor and Manage: Return to the Cisco AMP Console to verify that the connector is successfully connected and providing endpoint data. You can now monitor and manage endpoint security through the console.
- Regular Updates: It’s important to keep the Cisco AMP for Endpoints Connector up to date. Check for updates regularly to ensure you have the latest security features and enhancements.
Remember, the exact steps may vary based on the version of Cisco AMP and the operating system you are using. If you encounter any issues during the installation process, you can refer to Cisco’s official documentation or seek assistance from Cisco support.
IV. Synergy of AMP and Cisco Firepower
A. Amp in Cisco Firepower: A Unified Approach
The integration of Cisco AMP with Cisco Firepower creates a formidable partnership in the realm of cybersecurity. Cisco Firepower, a next-generation firewall, and intrusion prevention system (NGFW/IPS), combines its robust threat detection capabilities with the advanced malware protection prowess of Cisco AMP. This synergy fortifies network defense by offering real-time threat detection, prevention, and remediation, ensuring a multi-layered shield against a diverse range of cyber threats.
| Feature | Cisco Firepower | Cisco Advanced Malware Protection (AMP) |
|---|---|---|
| Intrusion Prevention | ✓ | ✓ |
| Next-Generation Firewall | ✓ | ✓ |
| Threat Intelligence Feed | ✓ | ✓ |
| Behavioral Analysis | ✓ | ✓ |
| Malware Detection | ✓ | ✓ |
| Real-Time Threat Updates | ✓ | ✓ |
B. Harnessing the Power of Cisco ThreatGrid
Cisco ThreatGrid, an integral component of the Cisco AMP ecosystem, contributes significantly to threat intelligence. It employs advanced sandboxing technology to analyze and dissect suspicious files and executables. By scrutinizing the behavior and attributes of potentially malicious elements, ThreatGrid delivers actionable insights to security teams, empowering them to identify and neutralize emerging threats swiftly.
C. Cisco Malware Protection: A Robust Shield
Cisco Firepower, coupled with AMP, provides a robust defense against malware in all its forms. The combined power of NGFW/IPS and advanced malware protection ensures that malicious activities are promptly identified, contained, and eradicated. Whether it’s known malware or elusive zero-day threats, the synergy between these solutions thwarts attacks before they can inflict damage.
D. Strengthening Network Defense with Endpoint Protection
The integration of AMP with endpoint devices creates a comprehensive defense strategy. Endpoints are the frontline of interaction with the digital landscape, making them vulnerable to a wide array of threats. With AMP extending its protective mantle to endpoints, organizations benefit from real-time threat intelligence, behavioral analysis, and continuous monitoring, ensuring that malicious activities are detected and mitigated across the network.
V. Cisco Talos: The Sentinel of Threat Intelligence
A. Meet Cisco Talos: The Threat Intelligence Team
At the heart of Cisco’s cybersecurity ecosystem lies Cisco Talos, an elite group of security experts and researchers. Talos tirelessly analyzes global threat data, identifies emerging vulnerabilities, and uncovers the tactics, techniques, and procedures of cybercriminals. This invaluable threat intelligence forms the bedrock of Cisco’s security solutions, including AMP, fortifying organizations against ever-evolving threats.
B. Leveraging Talos for Advanced Threat Detection
The insights generated by Cisco Talos elevate threat detection to a new level of precision. By constantly monitoring the threat landscape, Talos identifies indicators of compromise and potential threats, enabling security teams to take proactive measures. This early warning system enhances the organization’s ability to respond swiftly, mitigating risks before they escalate.
| Threat Category | Indicators of Compromise (IoC) | Threat Type |
|---|---|---|
| Malware | File Hashes, IP Addresses | Trojan |
| Phishing | URLs, Domains | Spear Phishing |
| Exploits | CVEs, Exploit Kits | Zero-Day Exploits |
| Command and Control (C&C) | Domains, IP Addresses | Botnets |
| Ransomware | Ransom Notes, Bitcoin Wallets | CryptoLocker |
C. Collaborating Cisco Talos with AMP for Unmatched Security
The collaboration between Cisco Talos and AMP epitomizes a holistic and proactive approach to cybersecurity. Talos enriches AMP’s threat intelligence with real-time data on emerging threats, ensuring that organizations remain steps ahead of cybercriminals. This partnership empowers security teams to make informed decisions, adapt strategies, and fortify defenses based on the latest threat insights.
VI. FAQs (Frequently Asked Questions)
A. What is Cisco Advanced Malware Protection (AMP)?
Cisco Advanced Malware Protection (AMP) is a comprehensive security solution that employs advanced techniques to detect, prevent, and remediate malware and cyber threats across networks and endpoints.
B. How does Cisco AMP contribute to cybersecurity?
Cisco AMP enhances cybersecurity by providing real-time threat intelligence, advanced malware detection, and rapid response capabilities, ensuring organizations are well-equipped to defend against evolving threats.
C. What are the key components of the Cisco AMP console?
The Cisco AMP console comprises the Cisco AMP Dashboard, which offers a visual representation of security activities, and the Cisco AMP Portal, a centralized hub for real-time threat intelligence.
D. What is the role of Cisco Secure Endpoint in AMP?
Cisco Secure Endpoint provides comprehensive endpoint security by utilizing advanced detection mechanisms, behavioral analysis, and machine learning to safeguard devices from malware and cyber threats.
E. How does Cisco AMP integrate with Cisco Firepower?
The integration of Cisco AMP with Cisco Firepower enhances network security by combining advanced threat detection and prevention capabilities, creating a multi-layered defense against cyber threats.
F. What is the significance of Cisco ThreatGrid in AMP?
Cisco ThreatGrid is a sandboxing technology that analyzes suspicious files and executables to deliver actionable threat intelligence, enhancing the detection and mitigation of emerging threats.
G. How does Cisco Talos enhance threat intelligence?
Cisco Talos, a team of security experts, continuously analyzes global threat data and shares valuable insights, enabling organizations to stay ahead of cyber threats and make informed security decisions.
VII. Conclusion
Cisco Advanced Malware Protection (AMP) is a pillar of defense and resilience in the constantly changing world of cybersecurity. Its complete strategy guarantees that enterprises have the tools and intelligence required to defend against a variety of threats, and is strengthened by the integration of Cisco Firepower, ThreatGrid, and the insights of Cisco Talos.
